C-UAS Factbook
7th Edition - November 2022
DroneShield C-UAS (Counter-UAS) Counterdrone Factbook covers key trends in the C-UAS market. This includes the review of the emerging UAS threat; categories of UAS threats, UAS types, and capabilities.
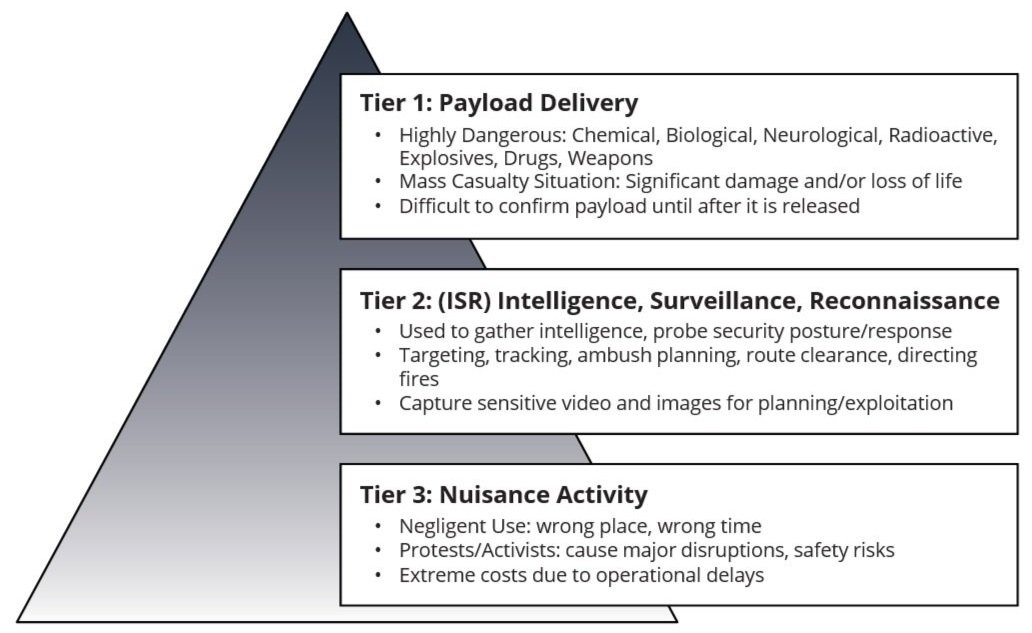
Primary threat categories include:
Nuisance Activity
Intelligence, Surveillance and Reconnaissance (ISR)
Payload Delivery
Different UAS types can include Unmanned Aerial Vehicles (UAVs), Unmanned Ground Vehicles (UGVs) and Unmanned Surface Vehicles (USVs).
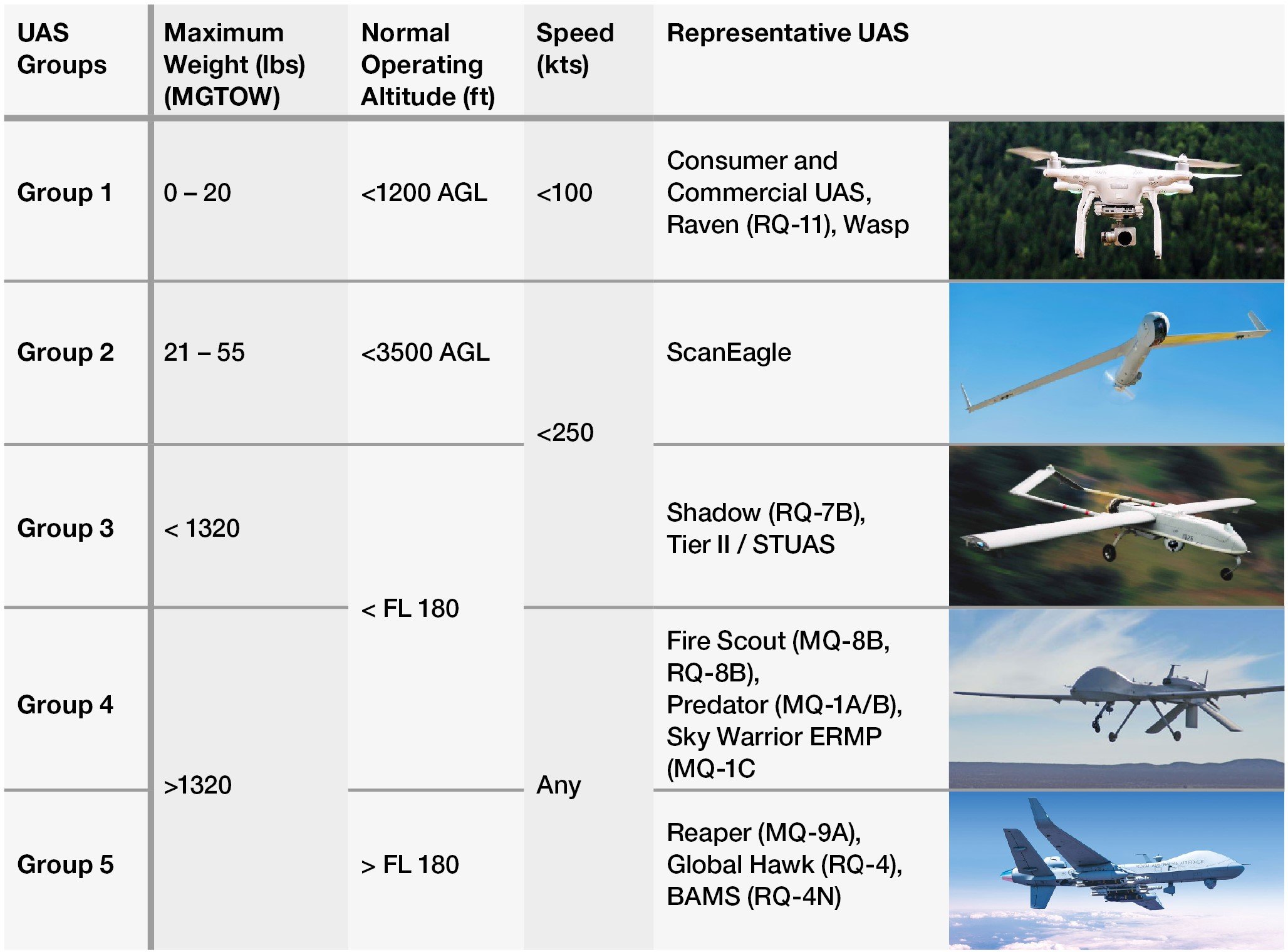
UAS types range from Group 1 (consumer and small UAS), all the way to Group 5, which include large military drones such as Reaper, Global Hawk, and others.
The C-UAS Factbook also considers various types of UAS detection sensors and methods, including radiofrequency (RF), radars, acoustics, optics, and multi-sensor systems. It also compares various UAS effectors, including jammers (RF and GNSS jamming), spoofing, hacking or protocol manipulation, directed energy, counterdrone drones, other kinetic solutions, and layered C-UAS defeat options.
Finally, this Factbook reviews types of counter-UAS providers, ranging from start-ups and project companies, to prime contractors, to established small businesses.
Table of Contents
Increased Risk and Widespread Threat
Notable UAS Incidents
Drone Use in Ukraine
Counterdrone in Ukraine
Drone Use in The Armenia/Azerbaijan Nagorno-Karabakh Conflict
Drone/UAS Types
State vs Non-State Solutions
Individual Drones vs Swarms
Chinese Drone Technology
Counterdrone 101
2. The Role of Counter-UAS Solutions
Detection Methods
Radio Frequency (RF)
Radar
Acoustic
Optics
Multi-sensor Systems
Defeat Methods
RF Jamming Technology
Global Navigation Satellite System (GNSS) Jamming
Spoofing, Protocol Manipulation and Cyber
Directed Energy
Counter-UAS Drones
Other Kinetic and High-Power Energy Solutions
Layered Defeat
Deployment Methods
Counter-Drone Countermeasures
3. Military Counterdrone Considerations
Counterdrone for Heavy Armor and Vehicles
Counterdrone for Littoral Vessels
Counterdrone for Military Bases and Critical Infrastructure
Counterdrone in Integrated Soldier Systems
Startups and Project Companies
Prime Contractors
Established Small Businesses
The Emerging Threat
Increased Risk and Widespread Threat
While the proliferation and beneficial applications for drone use increases, this growth equally increases the opportunities for bad actors to leverage these capabilities to carry out less than desirable operations.
Counter-UAS technology is still a relatively new industry and has only emerged with sophisticated offerings in the past few years. In less than a decade, just as with the UAS industry itself, the need for Counter-UAS capabilities has expanded to essentially every industry. Military, law enforcement and prisons might be obvious markets for C-UAS, however increased activity and threats have demonstrated the vulnerability that airports, critical infrastructure, and large public venues worldwide now face as well.
Perhaps no technology with military or “dual-use” application has evolved as quickly than the use of inexpensive drones, illustrated by their game-changing impacts on the battlespace during the Nagorno-Karabakh, Syria and Ukraine conflicts. State actors such as Russia, China, and Iran as well as non-state actors and terrorist groups like ISIS have developed and or demonstrated drone capabilities leveraging small UAS for military application. As the advances in drone technology and doctrine continue apace, the need to protect personnel and critical assets with layered and integrated counterdrone systems grows more urgent.
The Russia-Ukraine war is quickly becoming a textbook case study for the military application of drones. With all the tragedy, devastation, loss, and the high stakes of the conflict, it has also become a testbed for new military technologies.
The drone threat on the battlefield is here and quickly evolving, as currently seen in Ukraine and the Armenia-Azerbaijan conflict, and previously across the Middle East. Military and Border Security forces confront an escalating number of nefarious drones from both near-peer adversaries and asymmetric combatants, boasting increasingly lethal capabilities as technologies advance.
UAS serve as a new platform and delivery method for conventional threats such as payloads and surveillance.
The speed of capability advancement for even modest Commercial-Off-The-Shelf (COTS) drones provides a sobering example. In 2006 DJI was founded in a dorm room at the Hong Kong University of Science and Technology. A mere 16 years later, COTS drones, like DJI, today provide ISR, contraband delivery, direct attack, and fully autonomous flight against personnel and strategic assets. Russian Army General Yuri Baluyevsky said in August 2022 that the DJI Mavic’s capability to spot for accurate indirect artillery fire proved “revolutionary” in Ukraine.
Commercial technology advancements will continue to increase the threat level by incorporating swarming, thermal imaging, LiDAR, GPS-denied navigation, and more—with continuing performance enhancements in range (20km range is not unusual today), speed (close to 300km/hour recorded) and payload capacity (up to 20-30kg is routine for heavy-lift small drones).
These rapid advancements in COTS and nation-state drone capabilities have fueled the recent rise of counterdrone solutions as an adjacent solution requirement from the broader universe of Electronic Warfare (EW) capabilities. The ecosystem of counterdrone concepts and capabilities has grown rapidly, mirroring the advancements in drones themselves.
Modern warfare and tactics will continue to evolve. With two recent, full-scale wars, and the current fight in Ukraine, we now see asymmetric warfare tactics being adopted quickly by conventional forces.
Notable UAS Incidents
Real-world examples of the potential risk from drones aren’t limited to the battlefield. These stories range from clueless and careless operators obstructing emergency operations to more sinister attackers such as the UAS strikes on oil fields and attacks on government buildings and personnel. In the last few years alone, there have been highly visible incidents worldwide.
A few examples include:
Gatwick Airport (2018)
UAS activity reported within 1 km (0.62 m) of the airport
The reports caused major disruption, affecting approximately 140,000 passengers and 1,000 flights from Dec 19-21, 2018
Months later, April 2019, Gatwick had to close again and divert 3 flights due to an unconfirmed sighting of UAS
Saudi Aramco Oil Fields (Abqaiq-Kurais Attack) (2019)
UAS swarms were used to attack state-owned Saudi Aramco oil processing facilities at Abqaiq and Kurais in eastern Saudi Arabia
The attacks caused both facilities to close, reducing Saudi Arabia’s oil production by 50% (representing 5% of the global supply)
Attacks on U.S. Troops (2020)
U.S. troops from the West Virginia National Guard were confronted with a multi-day attack by small UAS (sUAS) dropping improvised explosives above them
The UAS and attackers could not be identified, however the mortar involved sophisticated 3D printed components
Armenia-Azerbaijan Border Conflict (2020)
In 2020, Armenia and Azerbaijan recommenced a long simmering conflict in the disputed Nagorno-Karabakh area, with extensive use of UAS by both sides, including small kamikaze/loitering munition drones
The conflict also includes Turkey, where a Turkish Bayraktar TB2 UAS was shot down by Armenian air defense units during fighting in Nagorno-Karabakh
Drone Contraband Delivery into Texas Prison (2022)
A DJI Inspire drone was allegedly flown into the airspace over FMC Fort Worth, a federal correctional facility
Affixed to the drone was a package containing 46 grams of crystal methamphetamine, 87 grams of pressed THC, two prepaid smartphones, and nine mp3 players
The drone crashed within the prison, where it was recovered by staff
Drone Use in Ukraine
Small to medium drones play a major role in the Ukraine war.
Precise payload delivery (such as dropping explosives or kamikaze attacks)
Fire-support ISR (directly providing fire coordinates and fire correction)
Tactical surveillance (providing cueing for more capable drones and improving individual ground unit situational awareness)
Psychological operations (soldiers “know” if they hear a drone, an attack is imminent. “Drone-shock” is the new shellshock)
Cyber/hacking (using proximity to the enemy networks to hack in via a drone, and then degrading/infiltrating the networks)
Image: UAS Threat Categories
Inexpensive drones symbolize asymmetric warfare in Ukraine, with $3,000 drones dropping charges that destroy $5 million armored vehicles and their operators.
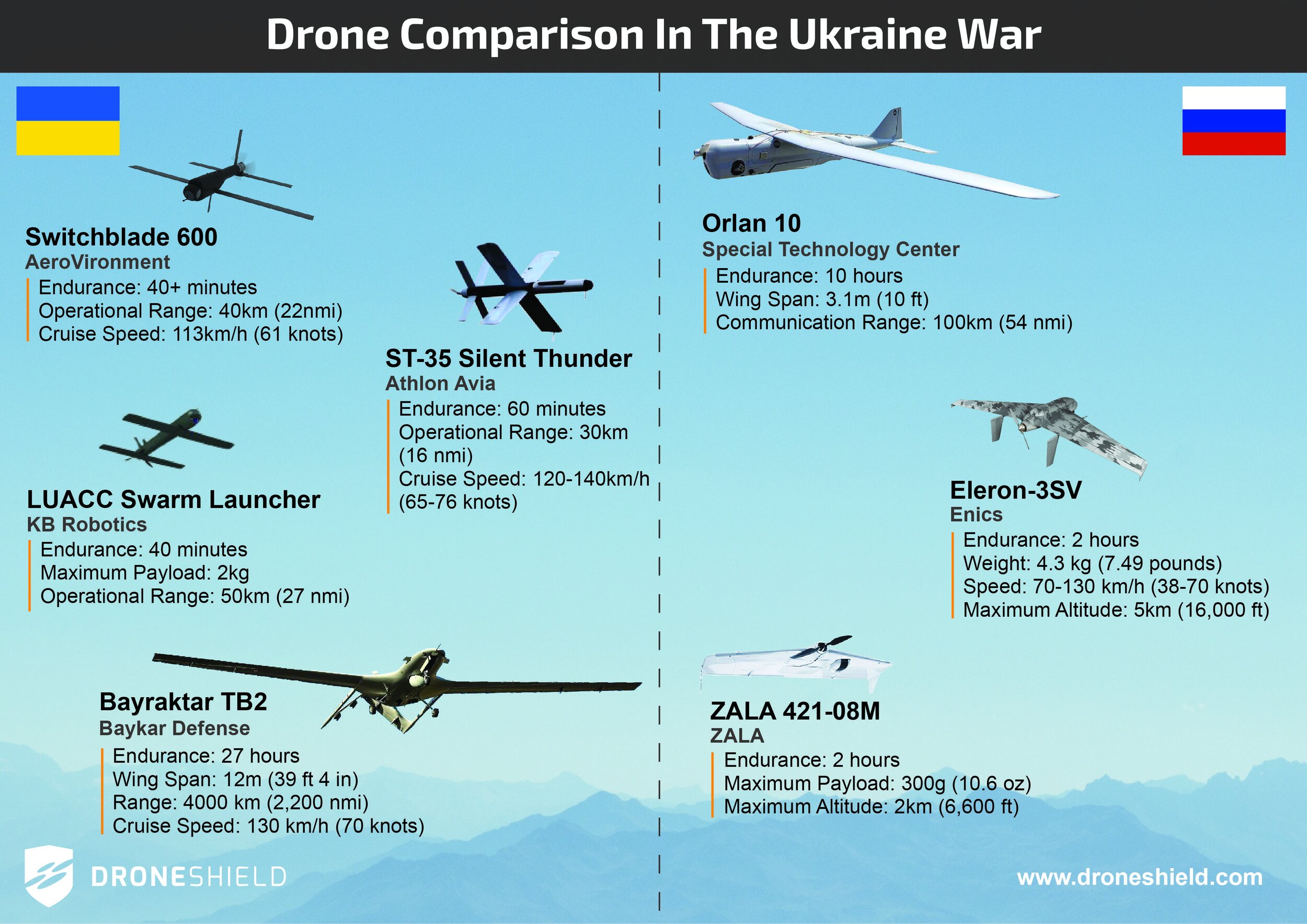
Russians use the following small/tactical drones:
Orlan-101 (Special Technological Center, St. Petersburg)—the most well-known Russian drone, with reportedly over 2,000 units made,
Eleron-3SV (Enics, Kazan)
Granat and the Takhion (Izhmash Unmanned Systems, Izhevsk)
Korsar (United Instrument Manufacturing Corporation, Moscow)
Zala-421 (Zala Aero Group, Izhevsk)
Irkut-10 (Irkut company, Moscow)
Observed Russian procedure is that if any one of the three aircraft were disabled, the other two would immediately return to base. All Orlans are fitted with a parachute for recovery. One exploit being considered by DroneShield is to activate the parachute using a method of protocol injection—this is yet to be developed but would be of extremely high tactical utility if fielded.
Image: Drone comparison in the Ukraine war
Ukrainians most famously use the Turkish-supplied TB2 Bayraktar, following their successful deployment by Azerbaijan in Armenia against the Russian supplied ground-defense Pantsir systems and tanks as well as in the Middle East. Prior to the war, Ukrainians planned a local manufacturing line for TB2s near Kyiv.
Some drones are designed and manufactured in Ukraine, such as:
UKRINMASH range of drones,
Ukrainian loitering Munition ST-35 drones, and
KB Robotics Loitering Munition drones.
Image: Bayraktar TB2
Counterdrone in Ukraine
Drones in a military conflict setting have proven challenging to defeat kinetically, either because of ineffectiveness of kinetic systems against swarms of small, fast moving drone targets, or due to cost asymmetry on ammunition or the actual system cost, vs cost of the drones.
Early counterdrone efforts fell into two categories at either end of a price/complexity spectrum. Low end systems solved only a tiny fraction of the overall counterdrone problem or compromised performance unacceptably to achieve cost-effectiveness. High end systems offered by traditional defense firms, frequently designed originally for broader purposes such as Electronic Warfare, were too expensive to be widely fielded (as well as being attractive targets to hit) and too complex for intuitive use by nontechnical end users.
This divide was on display in Ukraine, where the Russians deployed full-scale EW such as their vehicle-based systems, which are vulnerable targets and too expensive to field in quantities sufficient to provide ubiquitous protection.
On the other hand, the hand-held and portable units appearing in public reports seemed almost ‘homemade’. Such basic jammers likely jeopardize operator safety. Effectiveness is also in question; while signal jamming has been around since WWII, maximizing drone neutralization in the real-world today demands advanced intellectual property in waveform/antenna design, jamming signal effectiveness and effective heat dissipation.
How effective are Western counterdrone systems against Russian drones? Due to numerous factors, including the degradation and compromise of the Russian military-industrial base, there is widespread use of imported commercial components in Russian military systems. As an example, key Orlan-10 hardware is comprised of commercially available components from China, Europe, and the U.S. Counterdrone systems like DroneShield’s, which focus on commercial drones and components, are likely to be highly effective against threats like these for both detection and defeat.
Another recent drone innovation deployed in Ukraine is the small loitering munition, in this case the AeroVironment Switchblade, a low-cost flying smart bomb launched from a man-portable tube in the field and capable of destroying a tank.
Ukraine’s deployment of drones has been acknowledged as one key enabler of their asymmetric successes in defending against Russia’s overwhelming advantages in men and materiel. Open-source intelligence confirms Ukrainian drones dropping charges on Russian armored vehicles and scouting enemy positions with great success.
Russia expected a short war won through a lightning special forces leadership decapitation rather than an extended combined-arms conflict. This provided time for drone operators to learn how to maximize their destructive potential.
The Nagorno-Karabakh conflict and the Ukraine war demonstrated that drones (large and small) will be an integral and growing part of warfare in the near future however drones alone cannot win a war. Rather, drones have proven themselves as effective force-multipliers within combined-arms warfare, increasing the impact of infantry, artillery, and heavy armor—along air, sea, space, and even cyber domains.
Drone Use in The Armenia/Azerbaijan Nagorno-Karabakh Conflict
Both adversaries invested heavily in various drone types, from surveillance to direct-attack and loitering munitions. The results on the battlefield were described as game-changing, with doctrinal lessons for all armed forces.
Armored Vehicles were often unaware they had been geolocated until being attacked without warning. Azerbaijani forces relied heavily on Turkish-supplied drones (the same TB2 models used later by Ukraine), taking out vast numbers of Armenian combat vehicles. The drones were integrated with other assets, such as manned aircraft and artillery.
The use of affordable drones on the battlefield enabled effective payload delivery (either via the drone’s arsenal or by calling in precision strikes), with combat vehicles and Command and Control platforms seen as high value targets on the battlefield.
Drone/UAS Types
“Unmanned Aerial Systems” UAS is a broad term including everything from a $100 off-the-shelf UAS to a $1B military platform. It’s important to distinguish between the different types of UAS. The United States Department of Defense has created the following classification system for UAS:
Image: Department of Defense (DoD) UAS Group Descriptions
Smaller UAS (sUAS) classes are categorized as one of the following common types:
Image: Small UAS Types
Other types include Vertical Take-off and Landing (VTOL), a hybrid of the multi-copter and fixed-wing, and tethered drones, blimps, and kites. Adversaries have paired kites with burning fuel or explosives to drift downwind toward targets, i.e. “Kite Wars”.
Images: Ground and Water Surface Unmanned vehicles also present a threat, along with aerial drones
In addition to aerial (UAV) drones, other types include ground (UGV) and maritime (USV) domains, with generally similar detection and defeat technologies.
Note: Never use a drone that has been stolen from an adversary or found ‘crashed’ – these drones are likely boobytrapped, decoys and backdoored to get locations. Use caution when disassembling for parts.
State vs Non-State Solutions
Image: U.S. Navy’s Office of Naval Research launched Coyotes as part of its recent Low-Cost UAV Swarming Technology (LOCUST) effort
In addition to non-State actors adopting UAS for nefarious purposes, many militaries and other government agencies are increasingly including small UAS in their operations (as well as using COTS drones).
Russia has released a product for the helicopter gunship Mi-28NM, allowing it to fire mini-drones and suicide drones from the missile launch tubes.
Image: Russian Mi-28NM helicopter with mini-drone/suicide drone capability
Individual Drones vs Swarms
Drone swarms have become a reality over the last several years as the technology evolved. The swarm communication follows several models:
A human pilot controls each drone, where the pilots are coordinating.
All drones are completely autonomous on a set mission (using satellites for directions, for example).
"Master" controlled drones with "slave" drones. The "master" drone communicates to its "slaves" on it’s hosted network monitoring and updating their mission sets and objectives.
Effective counter-drone systems need the ability to detect and defeat swarms (potentially approaching from multiple directions simultaneously).
Chinese Drone Technology
As the home of DJI, the largest small drone manufacturer in the world, accounting for the majority of small drones, China has extensive capability in this space.
China has hundreds of drone models, with dozens of manufacturers involved. They range across traditional multi-copters, fuel cells, jet-powered, blimps, inflatable wings, gun-launched, swarm bombing systems and much more.
Aside from repurposed consumer drones like DJI, key providers include:
Beijing Institute of Technology (BIT): Falcon, M-5 Phantom, Miniature UAV, Gun-Launched UAV, Golden Swing
Harbin Engineering University (HEU): twin engine and rocket launched models
Shanghai UVS Intelligence System (UVSIS): S100, U650
Tian-Jie-Li Model: One, Skua, Talon, Mini Talon, Lotus
Chengdu Aircraft Design Institute (CDADI): CADI- 3, Coaxial Shape Varying Rotary Wing UAV, Mad Warrior, Rotary Dragon, Leap Dragon
Images: A Chinese UAS/drone fires from a launcher mounted to a Dongfeng Mengshi light tactical vehicle during a swarm UAS test by the China Academy of Electronics and Information Technology (CAEIT)
Counterdrone 101
Effective Counter-UAS Solutions typically offer one or a combination of the following capabilities: Detect, Identify, Track, and Defeat.
The primary objective of any C-UAS operation is to have situational awareness and protect their airspace. Depending on the risk or threat a drone poses and the authority of the user, the need to mitigate the drone may also be a mission objective. This can be achieved by stopping the drone (via hacking/takeover, jamming or kinetic means) or by locating and disrupting the operator (pilot).
The first step toward UAS protection is knowing when the threat appears, where it is located (or in the event of a swarm of UAS, where the multiple threats are located), and ideally where the source (or pilot) is located. While tracking the UAS in real-time, an appropriate response can be taken based on its location, e.g. apprehend the UAS pilot.
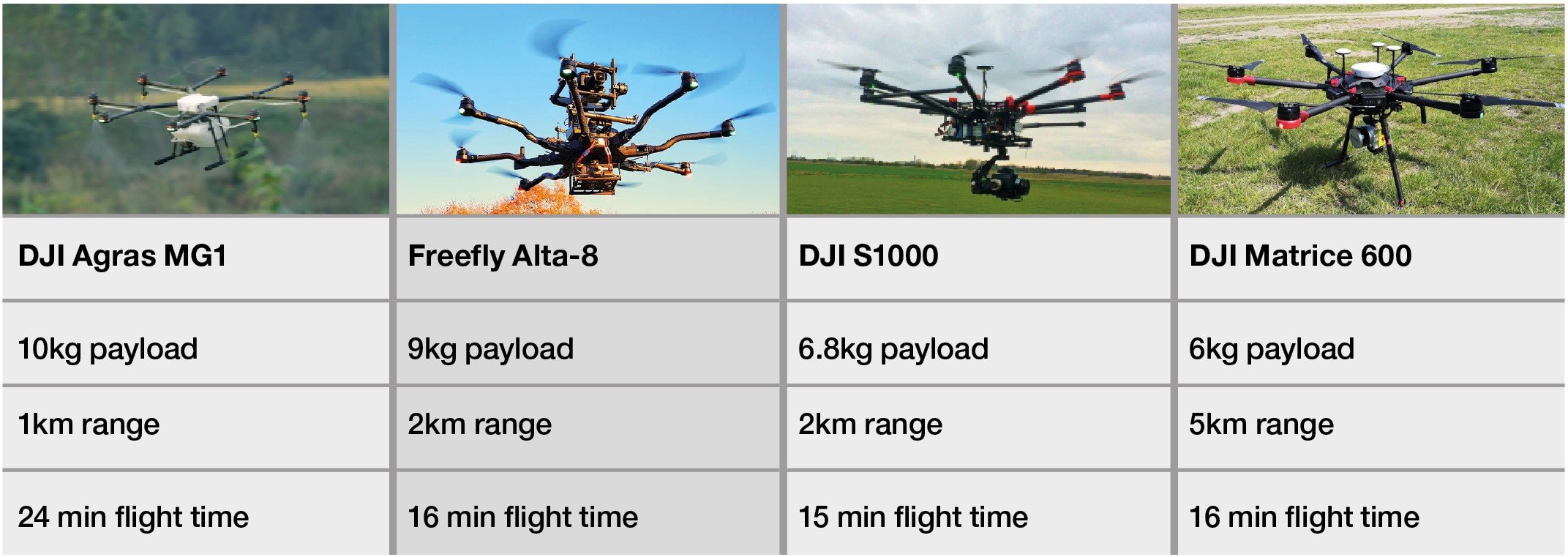
Identification of a drone, sometimes called classification is essential. Within Group 1 UAS, there is a considerable range of models—from under 100g (with short flight times and negligible payload capability) to UAS such as the DJI Matrice 600 which can lift over 6 kg. Determining whether the UAS carries a camera and/or additional payload is also relevant and can help assess the threat. Potentially valuable features of the drone include communications protocol and frequency, vendor/manufacturer, model, size/weight, speed and Radar Cross Section (RCS). The figure below depicts some of the larger Group 1 UAS examples. Although initially designed for agricultural use or large camera payloads, these UAS can easily be adapted to carry out warfighting.
Table 3: Examples of Heavy Lifting Small Drones
The Role of Counter-UAS Solutions
Detection Methods
1. Radio Frequency (RF)
Passive RF detection is the foundational layer of an effective counterdrone system. RF sensors provide detection capability by matching UAS communication protocols to known UAS RF signatures. Commercial and consumer-grade UAS use a variety of protocols, some of which are proprietary. RF- based detection systems that simply scan the frequency bands commonly used by UAS (for example, those that use Wi-Fi scanners or “sniffers”) run the risk of producing extremely high rates of false alarms.
RF sensors are typically “passive” in nature and do not broadcast or transmit. This allows RF counterdrone systems to operate without causing any interference for other communications on the network or in the operational area. The exceptions to the passive RF systems are those that actively use protocol manipulation, attempting to “hack” the UAS.
RF-based systems offer other desirable features in addition to their passive advantage. Required features will depend on the threat profile, and the following factors should be considered when evaluating RF solutions:
A large, upgradeable RF signature library or detection engine to provide high probability of detection and low false alarm ratios.
Ability to tag or filter false alarms to optimize and improve performance over time.
Azimuth and vertical coverage angles optimized for UAS or UAS detection, and
RF Direction Finding (RFDF) capability for UAS and controller.
RF sensors typically provide much greater detection range and cost-effectiveness than radar. The ability to DF based on RF can also provide geolocation capability similar to radar. RF can be an adaptable technology for UAS detection as evidenced by innovative solutions, such as body-worn, handheld, and vehicle-based products providing counterdrone capability in challenging field environments and during “on- the-move” operations.
As with all methods, there are challenges with RF that an effective system will need to overcome. Multi-path reflections are present in most real-world environments and can reduce accuracy. Multi-path means that the system receives a signal from multiple directions simultaneously due to signal reflection and a fit-for-purpose system will determine the true bearing of the UAS with a high degree of accuracy, despite the presence of multi-path signals.
Image: DroneShield’s RfOne Mk2 Sensor combined with Radar & EO
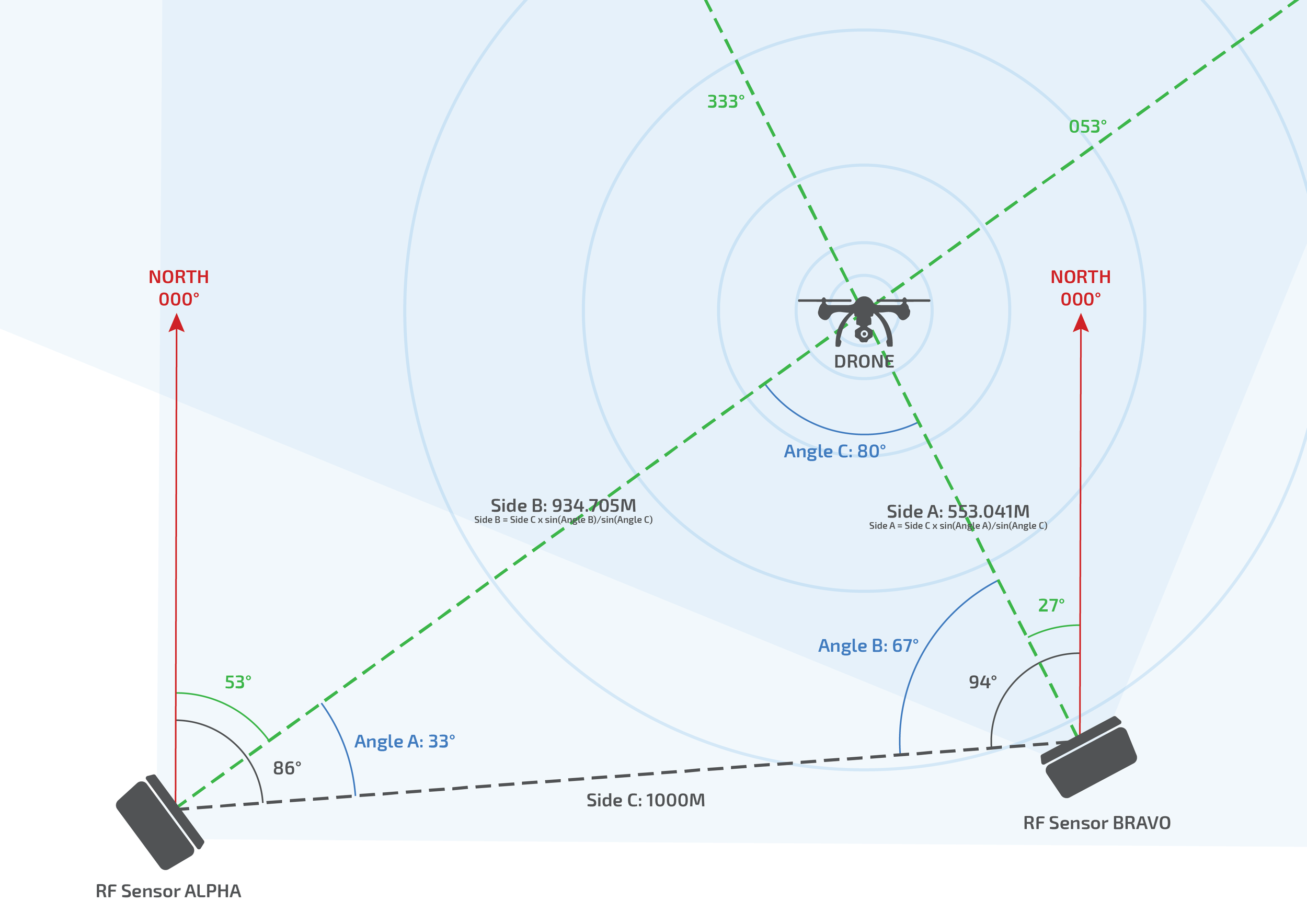
Image: RF intersection of a drone location (using two sensors)
Importantly, RF-based detection technologies come in a wide range of form factors, such as handheld devices in addition to being vehicle and fixed site products, giving additional versatility versus radars, which are more challenging to utilize in a portable capacity.
How will RF UAS detection (and defeat) technology evolve going forward?
With the advent of LTE-controlled drones, RF sensor technology must continue to evolve. Another common question is the performance of RF sensors against “autonomous” drones. While many so-called autonomous UAS still emit telemetry and video data, making it detectable to the RF sensor, completely RF-silent drones do exist. These UAS can be fitted with SD cards and use GNSS navigation or Inertial Navigation Systems, increasing their stealth, thus requiring reliance on other sensors to supplement RF.
There are four categories of UAS RF communications globally:
Remote Control (RC) hobbyist drones licenced for control in traditional shared hobbyist frequency bands. These bands are not designated for use outside of low baud rate telemetry control
Industrial Scientific and Industrial (ISM) band hobbyist UAS are essentially license-free but regulated in terms of applications, output power and spectral purity
Commercial drones, operational as compliant within allocated bands by the respective country’s civil regulator
Military drones, unregulated by civil regulators, which use traditional military communication bands, details of which are normally classified
Any RF-controlled UAS operating outside the first three categories are considered illegal, and intent to operate them contravenes the respective country’s governing radio communication laws.
There is already a proliferation of bolt-on third-party transceivers, modems and up/down converters offered that could be imported and used illegally. Competent counterdrone manufacturers keep up to date with these developments as they arise.
Counterdrone technology capability and innovation is growing exponentially, offering effective UAS and remote controller detection and countermeasure products to meet and challenge sophisticated UAS technologies where necessary.
Image: DroneShield RfPatrol body-worn drone detection device
2. Radar
A radar is effectively a motion tracker with broad application beyond UAS tracking. For counterdrone applications, the key is to use a radar that has sufficiently fine resolution to detect small UAS such as DJI Phantoms and smaller, at meaningful distances which is typically 1km or greater. Numerous radars, such as low-frequency pulse radar, have been designed to detect large metal objects like planes and helicopters but are poorly suited for detecting small radar cross sections or carbon-body objects that fly lower to the ground, such as Group 1 and 2 UAS.
Other considerations when evaluating counterdrone radar options include:
Dealing with ground clutter: Ground clutter can interfere with detection and generate false alarms from objects like trees and ventilation fans on building roofs, as these appear much like UAS blades to a radar. Advanced radar systems will apply various techniques to minimize this effect.
Azimuth Coverage: Azimuth is the horizontal coverage angle for radar. Typical ranges for a system are from 90 degrees to 360 degrees. For less than 360 degrees, multiple radars can be used to deliver a wider angle and larger coverage area.
Vertical Angle: The vertical angle of a radar tends to get overlooked. Many radars on the market have a narrow vertical angle, between 10-30 degrees, leading to potentially significant blind spots in vertical coverage. While a 90-degree vertical coverage is not usually needed, 40-80 degree detection is considered desirable.
2D vs 3D: 3D radar has several advantages over 2D, most notably, it provides elevation data on the drone. Also, it reduces clutter by filtering objects past certain heights and aids in eliminating ground- based false alarms.
Frequency Bands: Counterdrone radar bands include X-band (also commonly used on boats), K-band (originally used for self-driving cars but adapted for counterdrone), Ku-band and S-band (common with military deployments). The band used also influences the size of the radar. As an example, K-band radars typically offer smaller form factors.
Moving vs Fixed Panel: Depending on the use case fewer moving parts may be preferable, as this reduces wear and tear and the potential for damage. Some radars can be used in both “staring” and spinning mode, with staring mode providing better performance but a reduced coverage angle.
Radar Transmission Modes
Drone detection radars can utilize different technical approaches. Radars used in counterdrone solutions use one of the following three techniques: Pulse (active), Continuous Wave (active), and Passive mode. Each approach has different characteristics that might have advantages or disadvantages during operations depending on the requirements.
Active Radar - Pulse: Transmits a very short, but high-power pulse and waits for the reflected echo from the target. The performance is influenced by the duration of the transmitted pulses and the echo receiving time window. The shorter pulse duration results in a higher range resolution. Consequently, pulse radars are generally designed for long distances.
Active Radar - Continuous Wave: These radars continuously transmit an illumination signal and simultaneously receives echo reflections. A moving object’s speed and trajectory can be determined by observing its frequency shift, as seen at the receiver, due to the Doppler effect. Continuous wave systems are not able to perform range measurements without including a timing reference in the transmitted signal.
Passive Radar: Makes use of existing environmental broadcast, communication or radio-navigation transmission signals to detect the presence of objects in the receiver monitoring area. The system transmitter and receiver are at separate locations and the user only has control of the receivers. Potential illumination signals that could be used for UAS detection include FM, DVB, GSM, GNSS or WIFI. This approach is attractive for operations where end users prefer to use non-emitting devices so not to produce a noticeable signature during operations.
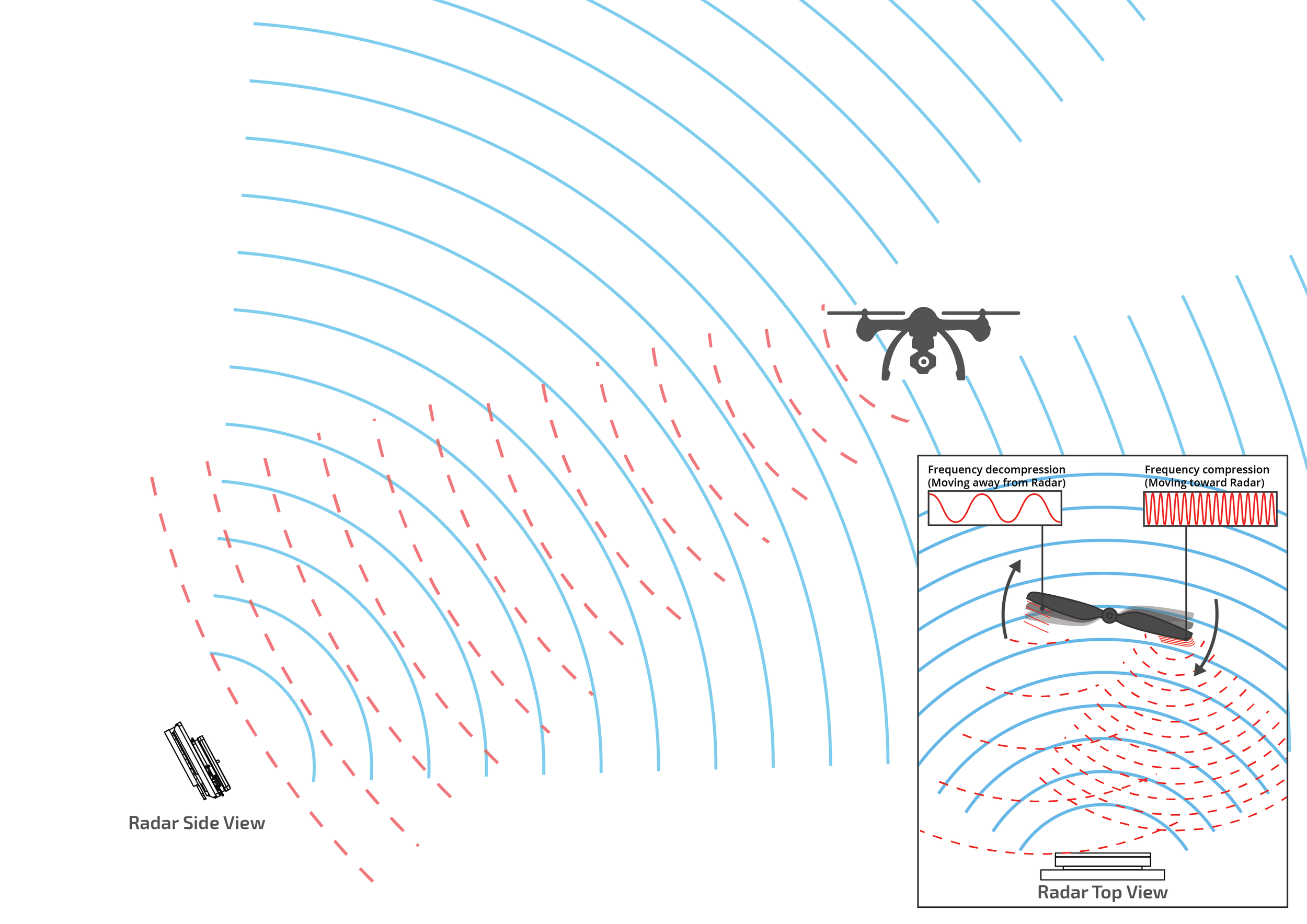
Image: Micro-Doppler Radar Detecting a Drone
Current Radar Developments
Radar manufacturers have been leveraging technologies like micro-Doppler and Artificial Intelligence to more accurately differentiate between UAS and other similar sized objects. As a potential technology obstacle, the micro-Doppler effect is expected to reduce significantly once UAS rotor blades are required by law to be covered by a protective cage (an expected safety development, given reported incidents of UAS blades causing body and eye injuries by UAS blades on contact).
Compliance
Compliance is an important part of purchasing a radar, as it is an active emitter. The FCC oversees certifications of radars in the US, OFCOM in UK, and similar organizations elsewhere globally.
3. Acoustic
There are two primary types of acoustic hardware used for UAS detection today – arrays and single- microphones. Arrays have the advantage of determining more precise location of the source; however, they are significantly more expensive with a larger form-factor than single microphone hardware.
Acoustic detection software works by removing the background clutter from noise made by the UAS blades and/or motor and comparing it to the database of acoustic signatures. Like early RF detection, multiple UAS map to “signatures” and a signature library and regular updates are needed to remain accurate and effective. It is worth noting that some of the more recent UAS are significantly quieter compared to earlier generations of drones, making the job of acoustic sensors more challenging.
Acoustic sensor technology is expected to respond well to AI, however to date it has not been incorporated in a meaningful way.
Advances are currently being made in acoustic detection, which can make them a viable complementary option or layer for counterdrone operations, however overall UAS detection capabilities based on acoustics still provide inferior standalone performance when compared to other methods such as radar or RF sensors.
Image: Squarehead Discovair Acoustic Drone Sensor next to DroneShield RfOne RF sensor
4. Optics
Electro-Optical (EO) and Infrared (IR) camera detection are popular components, often paired with other sensors, to produce integrated or multi-sensor counterdrone solutions.
Performance trade-offs between field of view (FOV) and distance need to be considered when using EO or EO/IR cameras. The greater the angle that is being monitored, the less the distance. Even expensive, high-quality cameras, with a 90-degree view, will struggle to detect a UAS much further than a few hundred meters without being initially cued by another sensor such as radar or RF.
Optical detection is another method that has benefited from recent advances in AI and computer vision. Even within the last 12 months, new techniques have emerged allowing high precision detection and classification algorithms for UAS to be developed.
Images: DroneShield’s DroneOptID Software detecting and classifying UAS. Red overlay represents pixels identified as ‘drone object’ tracked by the software
In a multi-sensor system, cameras can serve in a slew-to-cue function based on the detection provided by the primary sensors. The camera is directed toward the detection of known UAS activity and then can zoom on target and track. At this point, video analytics can provide further identification or capture image and video of the UAS activity as evidence of the UAS intrusion. More advanced analytics are useful for potentially identifying the drone’s payload and performing other autonomous threat assessment tasks.
5. Multi-sensor Systems
The main UAS detection methods today include RF, radar, and acoustic sensors, as well as optical and thermal sensors for further confirmation. A multi-sensor system will incorporate several or all of these into an integrated solution, providing multiple “layers” of detection. These layers can provide a more effective solution against diverse UAS threats as combining sensors often mitigates potential capability gaps of any single method. The inclusion of multiple sensors makes for a more comprehensive and complex system, however, can lead to a higher cost solution when compared to single method solutions.
More-exotic detection sensors exist, such as light detection and ranging or LiDAR, with limited application of as-yet-unproven effectiveness. There is no ‘one-size-fits-all’ counterdrone solution, and the role of the counter-UAS manufacturers and providers is to stay ahead of the constantly evolving commercial UAS technology.
Image: DroneShield’s DroneSentry Multi-sensor detection system
Defeat Methods
Defeat and mitigation solutions available in the counterdrone space today include both “soft-kill” and “hard-kill” (or kinetic) solutions. Soft-kill solutions involve methods that do not intentionally damage the UAS physically. Soft-kill methods include RF jamming or UAS “hacking”.
Hard-kill solutions physically affect the UAS with another object, projectile or directed energy. These solutions range from UAS seeking UAS, to kinetic solutions such as lasers and ammunition.
Soft-kill solutions typically carry less risk of collateral damage due to their non-kinetic nature and are more subtle and discreet in operation. As a result, hard-kill and kinetic methods are reserved for government use, and almost exclusively for military and federal-level use, with few exceptions. Although more widely used, even non-kinetic methods encounter varying levels of authority to operate, even among government agencies.
1. RF Jamming Technology
RF jammers transmit on the same frequency as a UAS uses to communicate with the controller or operator. When the jamming signal is stronger at the UAS than the controller’s signal to the drone, the UAS loses its connection and is forced into a pre-set emergency protocol to fly back to its starting point, hover or land.
Group 1 and 2 UAS communicate within known, unallocated frequency bands such as 2.4 GHz and 5.8 GHz. The UAS uses these frequencies to communicate with its controller and for First-Person View (FPV) video. UAS manufacturers are required to remain within the unallocated spectrum. Other less-common commercially used RF frequency bands include 433 MHz and 915 MHz ISM.
Jammer design may be directional or omni-directional (360-degree). Omni-directional jamming provides broader defeat coverage, while directional or sector-based solutions offer more precision and mitigate unintended interference.
Safety certifications are critical for jamming equipment. Cheaper equipment may expose the operator to sufficient RF energy to risk health over time (similar to some early C-IED equipment). Always insist on receiving safety certifications from accredited lab testing providers for any jamming equipment.
Jammers can integrate with the RF detection device—as one single device sharing the same antennas—producing a compact fully integrated detect-and-defeat solution.
While not a panacea for all possible drone-types, jamming is by far the most economical means of countering UAS. This means it is able to be fielded in much larger numbers to tactical level units, rather than being limited to specialist organizations.
2. Global Navigation Satellite System (GNSS) Jamming
American GPS may be the most known GNSS, but the GNSS systems of other nation-states also require attention: GLONASS (Russian), Galileo (European), BeiDou (Chinese), QZSS (Japanese) and NavIC (Indian). Commercial and consumer UAS frequently come with multiple GNSS capabilities.
If jamming a drone’s RF frequency, it may still utilize GNSS to fly back to its point of origin or continue along a pre-programmed navigation path. By jamming both the RF and GNSS, the UAS is severed from its communication and navigation links and cannot fly home or continue its pre-programmed flight path. Based on the drone’s capability, it may attempt to land once jammed or hover until it’s batteries drain.
3. Spoofing, Protocol Manipulation and Cyber
Spoofing or “hacking” involves a form of protocol manipulation. This method includes mimicking the controller and gaining control of the drone while acting as the controller. When successful, this defeat method allows the system to direct or reroute the UAS, which can be beneficial, especially for specific use cases. Spoofing can also include spoofing the GNSS signal, effectively misguiding the direction of the UAS.
A significant limitation of this approach is that the same or similar spoofing techniques are ineffective against all UAS, so there is always a risk of having a “hole” in the protection system. Even effective strategies are susceptible to software updates made by the UAS manufacturer or sophisticated UAS operators.
Notably, there have been false claims that protocol manipulation is legal for use. This is untrue, as it runs against the U.S. Wiretapping Act and other related legislation in the U.S. and globally.
Protocol manipulation/cyber and jamming are treated similarly under regulatory bodies insofar as they can be used only by Federal Government agencies under permissible circumstances.
Image: Hand-held Drone Jammers Provide a Point-and-shoot Functionality for Dismounted Operations
4. Directed Energy
Directed energy counterdrone methods include laser and high-power microwave systems. These methods are emerging, for use against Group 1 and 2 drones. Use of directed energy for counterdrone is still in its early stages and is currently being evaluated for military applications. They are generally more expensive systems.
Image: DefendTex Kamikaze Drone
5. Counter-UAS Drones
Autonomous Kinetic Defeat (Kamikaze) UAS and UAS-seeking UAS demonstrate novel kinetic approaches to defeat. Kamikaze UAS have limited commercial use as they essentially disable rogue UAS by physically damaging the UAS and knocking it out of the sky. Other UAS-seeking UAS catch or disable UAS with projectiles such as nets or modified rounds.
These techniques struggle to scale, especially against drone swarms, plus the kamikaze approach adds a high risk of collateral damage or injury.
6. Other Kinetic and High-Power Energy Solutions
The emergence of next-generation laser, high-power microwave and similar systems looks to provide sustainable kinetic defeat capability on the battlefield. Current key challenges remain around size, cost, and collateral impact of such technologies.
7. Layered Defeat
As with detection methods, layered defeat provides robustness and resilience against varied threats. Layered approaches can include soft- and hard-kill options or multiple strategies so the user can employ the ideal countermeasure based on real-time changes within the operational environment or objective. Layered defeat solutions may be impractical for the cost-conscious (or commercial) organization as many methods involve cost-prohibited or restricted technologies.
8. Deployment Methods
C-UAS systems are generally deployed in three ways:
Dismounted and Handheld
Vehicle, Ship and Aircraft Based
Fixed Site, Base Protection
It is important to select the right type of equipment for the job, as one size does not fit all – for example, a compact form factor is a priority for dismounted operations, while long range performance is a priority for fixed site systems.
Image: DroneShield DroneGun Mk3 handheld pistol shaped UAS jammer
Image: DroneShield DroneSentry-X vehicle mounted 360-degree detection and defeat countermeasure
Image: DroneShield DroneSentry autonomous detection and countermeasure fixed site system
9. Counter-Drone Countermeasures
With the continuous rise of UAS and C-UAS in military applications, there is an increasing focus on stealthy UAS that can resist defeat. Drones achieve RF stealth by neither taking instructions from the pilot nor sending any information back (such as location or sensor feeds). This is uncommon and sacrifices material capabilities (such as the inability to share recorded data or control payload release).
To achieve radar stealth, the UAS would need to remain motionless (as the radar is a motion tracker), without spinning blades while hovering (as radar can pick on the micro-doppler effect of the blades). This makes “radar stealth” very challenging for COTS UAS within commercial price brackets.
Regarding resisting defeat, designing a jammer-resistant UAS is challenging because of the need for control by the pilot or via satellite/GNSS. With both jammed, the UAS would need to rely on other technologies such as inertial navigation, which are at very early stages today for the requirements of UAS flights.
Military Counterdrone Considerations
DroneShield has set the global standard with a layered approach to counterdrone, with cost-effective mission-specific solution sets for:
Fixed site. The DroneSentry platform’s modularized long-range protection (detect, classify, track, defeat) can be provisioned with the right mix of sensor and effector modalities to suit the site’s threat profile.
Vehicular/shipboard/pop-up. The all-in-one DroneSentry-X offers fully integrated low-SWaP protection (detect, classify, locate, defeat) within a single housing, and
Handheld. RfPatrol and DroneGun deliver go-everywhere protection (detect, classify, locate, defeat) for dismounted soldiers.
Counterdrone for Heavy Armor and Vehicles
Heavy armored vehicles require supporting forward-deployed infrastructure such as fuel depots and field repair kits. However, much like many systems hardened against conventional attacks, they have vulnerabilities against small drones, as demonstrated in Nagorno-Karabakh and Ukraine.
Traditional small-caliber rounds have proven ineffective for counter-drone. A manually aimed attack will expend thousands of rounds while likely failing to neutralize a small, highly maneuverable drone further than a few hundred meters away, while tunnel-visioning on the drone and percussively divulging location to everyone nearby. A burst of well-aimed 30mm proximity rounds could be an effective, albeit expensive, answer, but it assumes that the crew detects the drone before it is above their firing arcs.
Large, armored vehicles are often unaware they have been geo-located until being hit without warning. A near-peer enemy will attack with Close Air Support or artillery; an asymmetric actor might swarm with DJI Phantoms armed with shaped charges or similar munitions. Commercial drones have many options for attack, but they typically come in very high and stay above the firing arcs. While DJI software limits the very affordable “Phantom 4” to 500 meters, the limit is easily disabled to capitalize on its service ceiling of 6,000 meters (or higher, with aftermarket communication range extenders such as DragonLink and RMILEC).
Image: DroneSentry-X Detect, Identify, Locate and Defeat
Counter-drone systems are beginning to appear more frequently on the battlefield for their ability to ‘listen out’ around the clock and identify expected or unexpected threats before reaching dangerous proximity. These systems—compact and sparing of precious vehicle real estate—are built with sensors that sweep the airspace around a vehicle to detect, classify and locate drones; then use either jamming defeat (especially overhead), or, when needed, kinetic defeat to mitigate the drone.
One such system is the DroneSentry-X, a fully integrated AI-based detect-identify-locate solution (with optional defeat).
DroneSentry-X offers real-time hemispheric 360-degree situational awareness and response capability on the move, with the flexibility to counter detected drones automatically or with an operator in the loop. DroneSentry-X can be deployed on a vehicle, tank, ship, other mobile asset, or as a pop-up solution, protecting a forward operating base, critical assets or fuel depots with local or remote operation. The system can be deployed in its standard variant or form-adjusted to the platform upon which it is mounted.
Counterdrone for Littoral Vessels
Compared with blue-water sailing, littoral operations occur in a higher near-shore risk environment—under the same threat from land-based drones as armor.
As such, the Littoral Maneuver Vessel-Medium (LMV-M) would benefit from a system such as DroneSentry-X. This concept was proven during a sea trial aboard the U.S. Navy’s stealth experimentation prototype vessel, the M80 Stiletto.
Multiple small USVs (3.5m long, 2m wide, and 1.8m in height, including the DroneSentry-X) would be deployed from the ship to provide a picket line of protection at a standoff distance. These USVs would be solar-powered, capable of 24x7 operation and autonomous station-keeping. At friendly ports, a counterdrone system can also be installed at the port itself.
Counterdrone for Military Bases and Critical Infrastructure
Depending on their location, size, and surroundings, the drone threat to fixed bases varies considerably. A one-size-fits-all solution could easily be either overkill, or inadequate to the nature of the threat. A peacetime domestic base concerned with protecting itself from nuisance or surveillance drone overflights would not need the same counterdrone protection as a wartime Forward Operating Base. However, it needs a similar architecture, so personnel have the training and the ability to forward deploy on short notice (noting that domestic base security in Australia is mainly outsourced, unlike forward deployments).
Therefore, an open and modular drone-protection platform provides the flexibility to match the protection to any specific threat level.
For example:
An expectation of fully autonomous drones could demand inclusion of radar and/or AI-based thermo-optical sensors to supplement RF sensors.
An environment with nearby civilian infrastructure, such as within an urban area, would demand precise zone-based alerting and response to prevent nuisance false alarms from, for example, drone flights in nearby public parks.
An environment without nearby civilian infrastructure could be a candidate for including kinetic countermeasures.
If swarming drones are a threat, robust RF disruption could be required to mitigate.
Multiple, layered levels of RF and kinetic disruption could be provisioned for the highest threat profile sites to ensure effective drone mitigation.
As counterdrone technology is in a state of constant advancement, investment protection (i.e., futureproofing) via modularity and open architecture are key. Any solutions should integrate seamlessly with complementary technologies and systems (such as base-security systems, a counterdrone Systems of Systems, and/or extant sensors) and rapidly incorporate ongoing innovations, maintaining superiority over the rapid-and-ongoing evolution of the drone threat.
Image: Forward Deployed DroneSentry Detect, Identify, Track and Defeat
Counterdrone in Integrated Soldier Systems
Individual warfighters are uniquely vulnerable to drones. In recent conflicts we have seen drones deliver small ordnance (such as grenades) directly onto unsuspecting warfighters. As such, individual personnel require situational awareness of drone operations in their immediate area.
Furthermore, soldier-mounted and body-worn systems, combined with tactical or MANET radios can allow individual platoons to act as a distributed network of counter-drone situational awareness and defeat capabilities for the wide battlefield. Counter-drone systems are already becoming a core component of force protection and Intelligence, Surveillance, Reconnaissance and Electronic Warfare (ISREW) capabilities of the dismounted personnel.
Integrated battlefield solutions of the next decade will need counterdrone systems that are capable of the following:
Interoperable, easily integrated existing systems such as ATAK
Compatible with standard with standard interfaces
Can leverage existing mission tools and standard components, such as common batteries and cables already used by other fielded equipment
Low Size, Weight, and Power (low-SWaP)
Ruggedized and operational in extreme environments
Several approaches to counter-drone exist for the dismounted soldier:
Body-worn passive drone-detection systems. Products like DroneShield’s RfPatrol provide early warning to individual soldiers of drone operations in the vicinity. These systems are approximately the same SWaP as a MANET radio and provide warning of drones in a vicinity of 2- 4km. Such systems can also be networked to communicate drone detection information across platoons and to command-and-control centers, providing situational awareness across the distributed forces.
Mounting of vehicle-based systems like DroneSentry-X on manned or unmanned ground vehicles. This reduces weight and equipment on the operator while providing drone detection and defeat capability in a single form factor.
Handheld jamming devices. Handheld drone jammers provide a simple and effective method of drone defeat that an individual soldier can utilize with point-and-shoot simplicity. Ongoing enhancements in these jammers have reduced their SWaP while increasing their effective range.
Image: Body-worn RfPatrol Mk2 Provides Early Drone Detection and Integrates with Existing PTT Systems, Conformal Batteries, ATAK and Standard Radio Batteries
Counter-UAS Providers
With counter-UAS technologies rapidly coming to market to address the quickly growing UAS threat, it becomes increasingly difficult for the prospective users of the technology to identify cost-effective and high-performance solutions for their specific needs.
Typically, there are three types of solution providers:
1. Startups and Project Companies
Counterdrone is a growing industry now, with numerous startup companies entering every year. The origins of counterdrone startups vary, but many times are a result of development projects or licensing specific technology or intellectual property and building a product around it. Innovation coming from startups can be encouraging, however stability of a startup company should also be a point of focus. Commercial UAS technology is advancing at a rapid pace. As important as a company’s capability today is their engineering team’s vision and technical ability to scale, maintain their solutions, and advance the capability along with the fast moving commercial and after-market sectors. Many companies in this space have not yet acquired the necessary team expertise or resources to execute in one or more of these areas.
Startups and project companies can possibly offer users beneficial options, such as cost-effective products and an innovative approach to the problem. Considerations and potential trade-offs come with the company’s ability to maintain relevance and performance against constantly evolving commercial developments, as well as overall quality, sustainability, and on-going support for purchased products.
2. Prime Contractors
Prime Contractors and large System Integrators typically can offer significant capabilities in the Counter-UAS market. In the past few years, leveraging their access or previous development of high-end solutions for different scenarios, such as mortar detecting radars and IED jammers, large Primes have re-purposed some of these technologies for their new Counter-UAS offerings. Prime solutions also utilize existing products such as Radars or RF sensors from third-party companies that have specialized expertise in their respective fields to provide a larger “system of systems” or more complete layered solution.
A key consideration is the typically higher price of a prime solutions, which makes most of the solutions only feasible for the military. Also, re-purposing or “Multi-use” technology such often come with trade-offs or gaps in capability when compared to a technology built specifically for the nuances of UAS operations. Timelines and restrictions are other factors as these technologies often result from multi-year development programs funded by the customer, and therefore can be subject to restrictions for export or commercial use.
3. Established Small Businesses
In the middle are companies that have survived their startup growing pains, have industry expertise in a relevant area, and can offer the agility of a dynamic team. At this stage, these companies should have evolved from a single-product company and have proven ability to scale production to meet the demand of larger customers. They typically have a funding base and or source of revenue that provides stability for their on-going development and support for their customers.
Counter-UAS is not a one-size-fits-all solution, therefore, its beneficial to seek a company that is committed to continued development and has demonstrated success with rapid product development to address evolving commercial technologies. Capable companies in this space should offer that desired balance of counterdrone focus and agility, which are both needed to field superior solutions.
Growth looks different for every company, therefore, established small businesses present various levels of product maturity, quality control, customer support, and most importantly, in-house counterdrone development expertise. Things to consider when evaluating counter-UAS providers are; their engineering team and capability, more than a single product or solution, and vision and evidence of future product development. The company’s ability to scale production, support deployed solutions, and meet customers’ unique requirements are also imperative for a successful solution and the success of your counterdrone operations.
Legal and Compliance Considerations
Laws surrounding purchase and use of counterdrone equipment are continuing to evolve, attempting to keep up with the developments of the drone technology. There are various laws and regulations to consider around drones, drone use and counterdrone technology. The applicable laws vary significantly between different locations and organizations and are subject to change and evolution. In the US, the most relevant restrictions are around FCC and FAA.
The FCC regulations stipulate how much energy can be emitted from various equipment at various frequency bands, and generally radars and jammers (as well as cyber/protocol manipulation) falls within their coverage. This means either a license is needed (the common approach with radars), or the FCC regulations need not to apply to a particular user in a given situation – such as military, DOJ or FBI in certain situations. As a basic rule, jammers (or protocol manipulation/cyber) are off-limits to individuals, corporations, state and local Government agencies (however drone detection equipment can still be used by them). Outside of the US, similar rules are in place by Ofcom (UK) and ACMA (Australia).
The FAA regulations essentially treat a drone like any full-size aircraft, and prohibit ‘downing’ of the drones by private citizens, in the same way as downing of the full size aircraft is not allowed- therefore limiting the defeat to military and federal Government agencies.
Export and import provisions may also apply, depending on where the equipment is made, where it’s going to, and whether it’s considered for military-civilian dual use or military-grade article. In the US, the relevant restrictions are around USML (Munitions List) classifications, whether the products are ITAR-grade, ECCN, EAR99 or other classification. An experienced counterdrone manufacturer can work with the customer to ensure compliance with the export control laws.
What Next?
Layered counterdrone systems will become a critical component for many assets, such as tanks, supply depots and other infrastructure. Defense will benefit by forming a long-term relationship with an experienced sovereign partner to manage the current and future drone threat. DroneShield offers the proven capability and expertise for this key role, to work collaboratively with industry partners and academia—while leading the delivery of counterdrone solutions.
DroneShield offers to build on the foundation of our ongoing commercial successes by sharing development risk with Defense, relying in part on an internal funding model, having raised over $50 million in private funds over last 7 years. DroneShield engages with dozens of subcontractors, ranging from the manufacture of complex parts to finished product assembly and testing (in addition to in-house manufacturing capabilities).
There are many considerations to make when evaluating counterdrone options. Identifying the right solution for your organization requires a clear understanding of your objectives, due diligence, and the right solution provider.
Demos are a common way to get a feel for the solution and ask any questions, both on the setup/integration with the existing security systems, and on the operations. Given the nascent stage of the industry, there is a need to ensure integrity of the demos and doing setup in representative conditions, including:
Supplying own drones where possible (there have been reports of unscrupulous vendors attaching transponder beacons to drones to falsely improve the performance of their detection systems)
Set up demos in the environments where the products will be deployed, as opposed to an ideal setup (an open field is more forgiving than a city environment).
Aside from the technical aspects, other considerations that may influence your decision can include;
Overall costs of operation
Current regulations and restrictions
Operational area and environment
Standard Operating Procedures for the organization
For more information on how to implement the best solution for your project or any other counter-UAS related questions, please contact us at info@droneshield.com